Cyber Security
 3 min read
3 min read
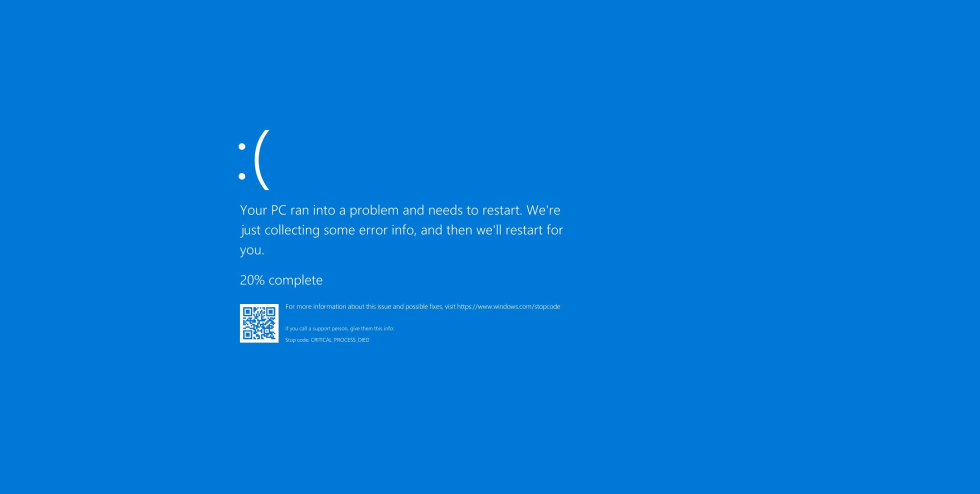
Major Global Outage Triggered by CrowdStrike Update Causes BSOD
On Friday, a significant update from CrowdStrike, a leading endpoint security software provider...
 2 min read
2 min read
The WannaCry Malware
Everyone has heard of ransomware came out this year called ‘WannaCry.’ I was not a...
The Importance of Comprehensive Security: Beyond the Perimeter
When it comes to safeguarding a company, the most devastating attacks often come from within rather...
 2 min read
2 min read
EAP over MS-CHAP version2 Preferred Method of Remote Access Authentication
Extensible Authentication Protocol (EAP) is an authentication framework that is used in wireless...
 3 min read
3 min read
Advantages and Disadvantages of the Use of Mobile Devices for Business Operations
According to a recent study, 75 percent of IT security professionals said that mobile devices will...
 1 min read
1 min read
AAA Server
AAA Server Features TACACS+ RADIUS Most often used for Network devices Users Transport protocol TCP...
Network Security: Tools and Methodologies
With the increasing number of connected individuals, understanding network security is paramount...
 11 min read
11 min read
Adequate Societal and Political Awareness in Cyber Crime
January 11th, 2011 It is evident that many companies still lack security, at the same time carrying...

